31. Basis path testing falls under
(A) System testing
(B) White box testing
(C) Black box testing
(D) Unit testing
Answer: (C)
32. The User Work Area (UWA) is a set of Program variables declared in the host program to communicate the contents of individual records between
(A) DBMS & the Host record
(B) Host program and Host record
(C) Host program and DBMS
(D) Host program and Host language
Answer: (B)
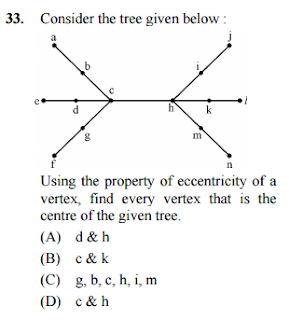
Answer: (A)
34. The maximum number of keys stored in a B-tree of order m and depth d is
(A) md + 1 – 1
(B) (md+1 – 1) / (m – 1)
(C) (m – 1) (md + 1 – 1)
(D) (md – 1)/(m – 1)
Answer: (B)
35. Which of the following is the most powerful paring method?
(A) LL (I)
(B) Canonical LR
(C) SLR
(D) LALR
Answer: (C)
36. In UNIX, which of the following command is used to set the task priority?
(A) Init
(B) Nice
(C) Kill
(D) PS
Answer: (D)
37. AES is a round cipher based on the Rijndal Algorithm that uses a 128-bit block of data. AES has three different configurations. ______ rounds with a key size of 128 bits, ______ rounds with a key size of 192 bits and ______ rounds with a key size of 256 bits.
(A) 5, 7, 15
(B) 10, 12, 14
(C) 5, 6, 7
(D) 20, 12, 14
Answer: (D)
38. Match the following IC families with their basic circuits:
a. TTL 1. NAND
b. ECL 2. NOR
c. CMOS 3. Inverter
Code:
a b c
(A) 1 2 3
(B) 3 2 1
(C) 2 3 1
(D) 2 1 3
Answer: (C)
39. Match the following with respect to C++ data types:
a. User defined type 1. Qualifier
b. Built in type 2. Union
c. Derived type 3. Void
d. Long double 4. Pointer
Code:
a b c d
(A) 2 3 4 1
(B) 3 1 4 2
(C) 4 1 2 3
(D) 3 4 1 2
Answer: (C)
40. Given an empty stack, after performing push (1), push (2), Pop, push (3), push (4), Pop, Pop, push (5), pop, what is the value of the top of the stack?
(A) 4
(B) 3
(C) 2
(D) 1
Answer: (D)




No comments:
Post a Comment